Leaps Model Of Communication
Global Affairs Canada Hit by Cyberattack. Cougar House Ep.

North Staffordshire Combined Healthcare Listening And Engagement Active Partnerships Leap
Big data analysis challenges include capturing data data storage data analysis search.

. Relevant items of information include a persons actions feelings ideas beliefs values and things in the environmentCognitive dissonance is typically experienced as psychological stress when persons participate in an action that goes against one or more of. There once was a time when finance professionals were bound to cubicles but that era is long gone. Model Prisoner 479 NO BOUNDARIES.
Lick the plate clean COUGAR. It provides one-stop access to the best in both reference material and cutting-edge research and is my starting point for every new project David Danks Professor of Philosophy Psychology Carnegie Mellon University Foundational and Cutting-Edge Content MIT. A breach or a lunge is a leap out of the water also known as cresting.
Research in Outdoor Education is a peer-reviewed scholarly journal seeking to support and further outdoor education and its goals including personal growth and moral development team building and cooperation outdoor knowledge. The latest news and headlines from Yahoo. Breaking news from the premier Jamaican newspaper the Jamaica Observer.
Using a logic model to focus health services on population health goals. Part of the added value of logic modeling is that the process creates a forum for scrutinizing big leaps of faith a way to searching for unintended effects. Boxy 3000 has been re-invented and given an extra 2000.
Game overlet the boys claim her soul. Cetacean researcher Hal Whitehead defines a breach as any leap in which at least 40 of the animals body clears the water and a lunge as a leap with less than 40 clearance. Its also worth considering how much better off the industry might be if Microsoft is forced to make serious concessions to get the deal passed.
More and more users and businesses use smartphones not only to. Boxy 3000 was the earlier model of the trainee chatbot. Qualitatively a breach is a genuine jump with an intent to clear the water whereas.
A - Asking questions this will allow you to act consistently and fairly with people. The distinction between the two is fairly arbitrary. Over Half of Medical IoT Devices Found Vulnerable to Cyberattacks.
In business theory disruptive innovation is innovation that creates a new market and value network or enters at the bottom of an existing market and eventually displaces established market-leading firms products and alliances. Telehealth is the use of digital information and communication technologies to access health care services remotely and manage your health care. These days any perception that finance skills involves simply crunching numbers has been replaced by the reality that positions require workers to deal with clients every day.
And enhances communication with external audiences such as the media or potential funders. You can achieve this by applying the following LEAPS. Government to Adopt The Zero-Trust Security Model.
Exhibitionist Voyeur 080119. Mobile security or mobile device security is the protection of smartphones tablets and laptops from threats associated with wireless computing. Formally a string is a finite ordered sequence of characters such as letters digits or spaces.
ASCII characters only characters found on a standard US keyboard. 6 to 30 characters long. A loanword also loan word or loan-word is a word at least partly assimilated from one language the donor language into another language.
In the field of psychology cognitive dissonance is the perception of contradictory information and the mental toll of it. Safe Cracker 475 Eric takes Margo to the Bank. It also marks a new model for delivery where subscribers can expect to get more frequent updates with new features and improvements.
Technologies can include computers and mobile devices such as tablets and smartphones. E - Empathy show an understanding to the person and try to put yourself in their situation. But wait a second time.
Open source is source code that is made freely available for possible modification and redistribution. 10 little-known keyboard shortcuts for editing in PowerPoint If you use PowerPoint at work or at home keyboard shortcuts can be a great time. Get breaking news stories and in-depth coverage with videos and photos.
A main principle of open-source software development is peer. Wont this bring about the machine apocalypse. This is in contrast to cognates which are words in two or more languages that are similar because they share an etymological origin and calques which involve translationLoanwords from languages with different scripts are usually.
Exhibitionist Voyeur 072319. The empty string is the special case where the sequence has length zero so there are no symbols in the string. Tips and guides Microsoft 365 Enterprise Published August 13 2015.
Breakfast of Champions 479 Eat up. Not just yetBoxy 5000 is more advanced and learns as they go but Skynet is. We are learning from some design flaws and moving forward with a more advanced bot.
Products include permission to use the source code design documents or content of the product. After more than twenty years Questia is discontinuing operations as of Monday December 21 2020. Research in Outdoor Education.
Must contain at least 4 different symbols. The concept was developed by the American academic Clayton Christensen and his collaborators beginning in 1995 and has been called. 89 of Organizations Are Non-compliant With CCPA Law.
Big data refers to data sets that are too large or complex to be dealt with by traditional data-processing application softwareData with many fields rows offer greater statistical power while data with higher complexity more attributes or columns may lead to a higher false discovery rate. On the other hand Sonys fixation on Call of Duty is starting to look more and more like a greedy desperate death grip on a decaying business model a status quo Sony feels entitled to clinging to. L - Looking listening and communicating professionally.
News on Japan Business News Opinion Sports Entertainment and More. The computer-driven model used to make decisions may not be right for you if you have a complex medical history. CogNet MIT Press CogNet MIT CogNet is an invaluable resource for all cognitive science research.
Positive communication will go a long way towards preventing conflict. Follow Jamaican news online for free and stay informed on whats happening in the Caribbean. It has become increasingly important in mobile computingThe security of personal and business information now stored on smartphones is of particular concern.
The open-source model is a decentralized software development model that encourages open collaboration. Find in-depth news and hands-on reviews of the latest video games video consoles and accessories.

Communication Officer Hi Res Stock Photography And Images Alamy

Aquacycle Leaps Forward Through Active Involvement Of Tunisian Women Researchers Eni Cbc Med

Giant Leaps Literacy Advice Clinic St Joseph S

Leaps Initiative Leapsinitiative Twitter
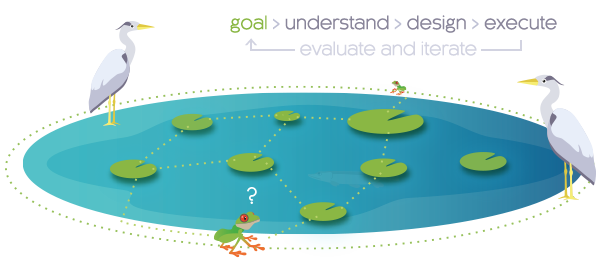
What You Need To Know Before You Make The Jump Frogleaps

Making Progress For All Learners Through Leap Children S Institute
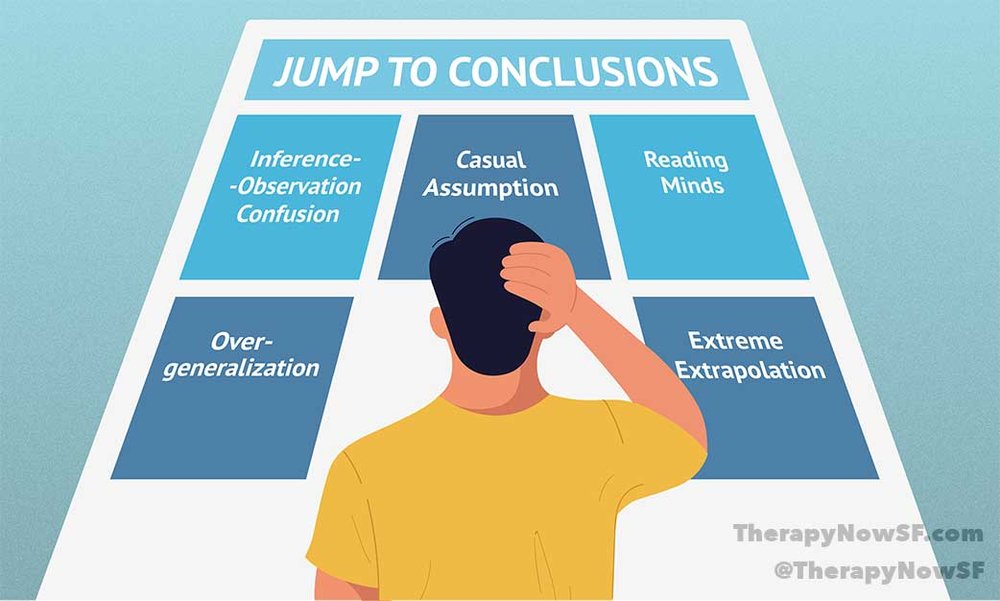
Jumping To Conclusions Learn How To Stop Making Anxiety Fueled Mental Leaps Therapy Now

848 Get Better At Communication Tiny Leaps Big Changes Podcast On Goodpods

Leap To Solve Customer Issues
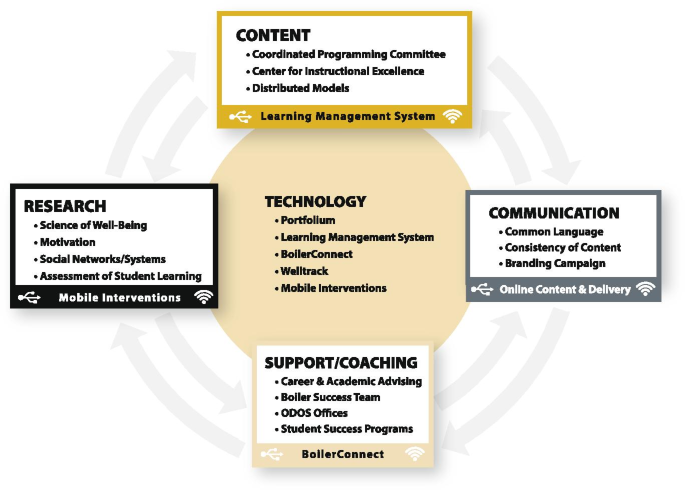
A Holistic Approach To Campus Well Being Steps To Leaps At Purdue University Springerlink

Leaps Innovative English Methodology Last 2 Days For Early Bird Registration Teaching Is Not Enough We Cannot Act On What We Do Not See This Is At The Grassroots Of Both

Conflict Resolution Training Ppt Video Online Download
Ada Health Closes 90m Series B Led By Leaps By Bayer Techcrunch

Weekly Round Up How To Improve Your Communication By Leaps And Bounds Achieve Your Leadership Vision By Increasing Clarity Creating Organizational Change

How To Improve Your Communication By Leaps And Bounds

A Leaps Model Illustrating The Interactions Of Learner Characteristics Download Scientific Diagram
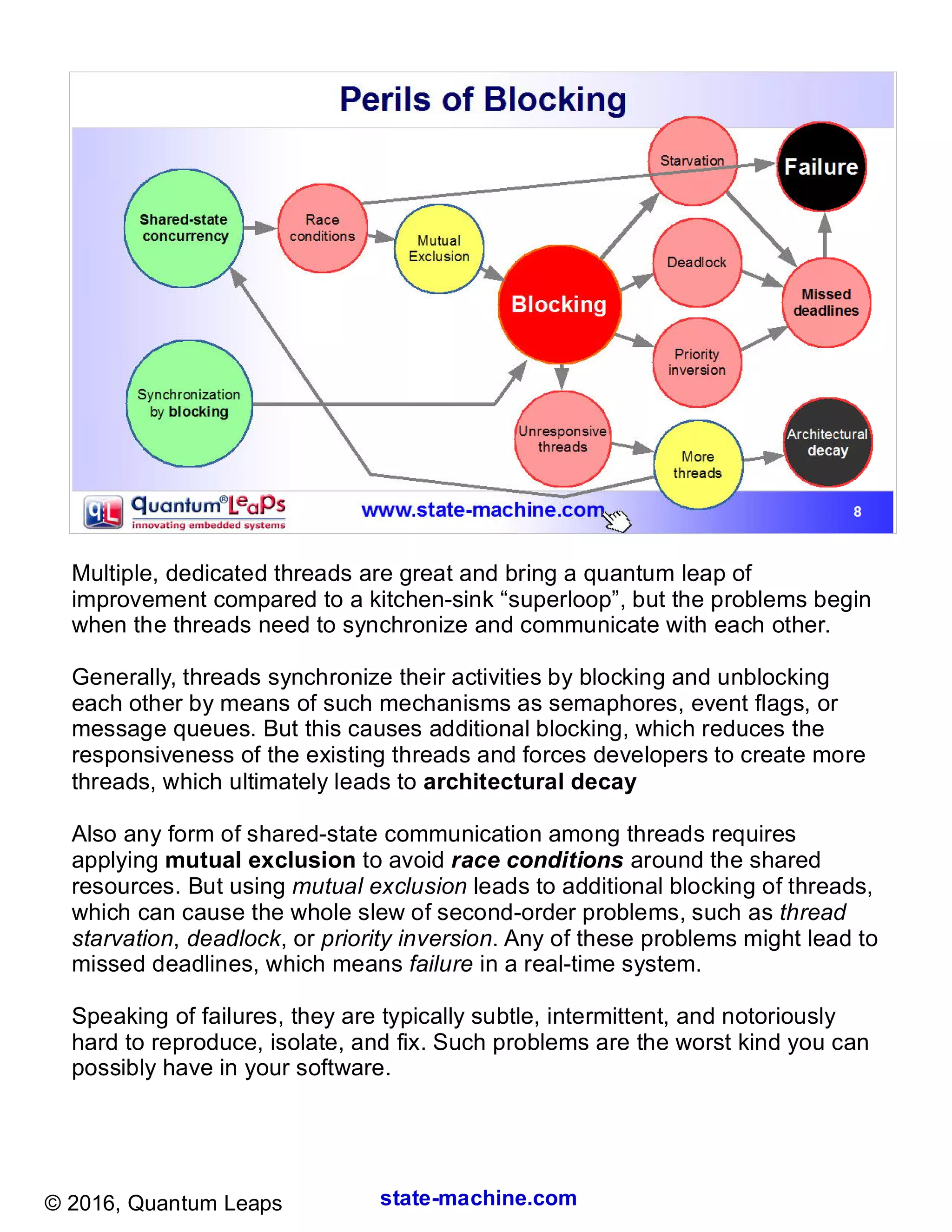
Beyond The Rtos A Better Way To Design Real Time Embedded Software